Scope/Description
- This article will walk through the process of joining an Active Directory in Houston UI with Rocky Linux.
Prerequisites
- Rocky Linux 8
- Houston UI
- Windows Active Directory
- Credentials for Domain User with permission to authenticate Active Directory Join
Steps
Installing packages
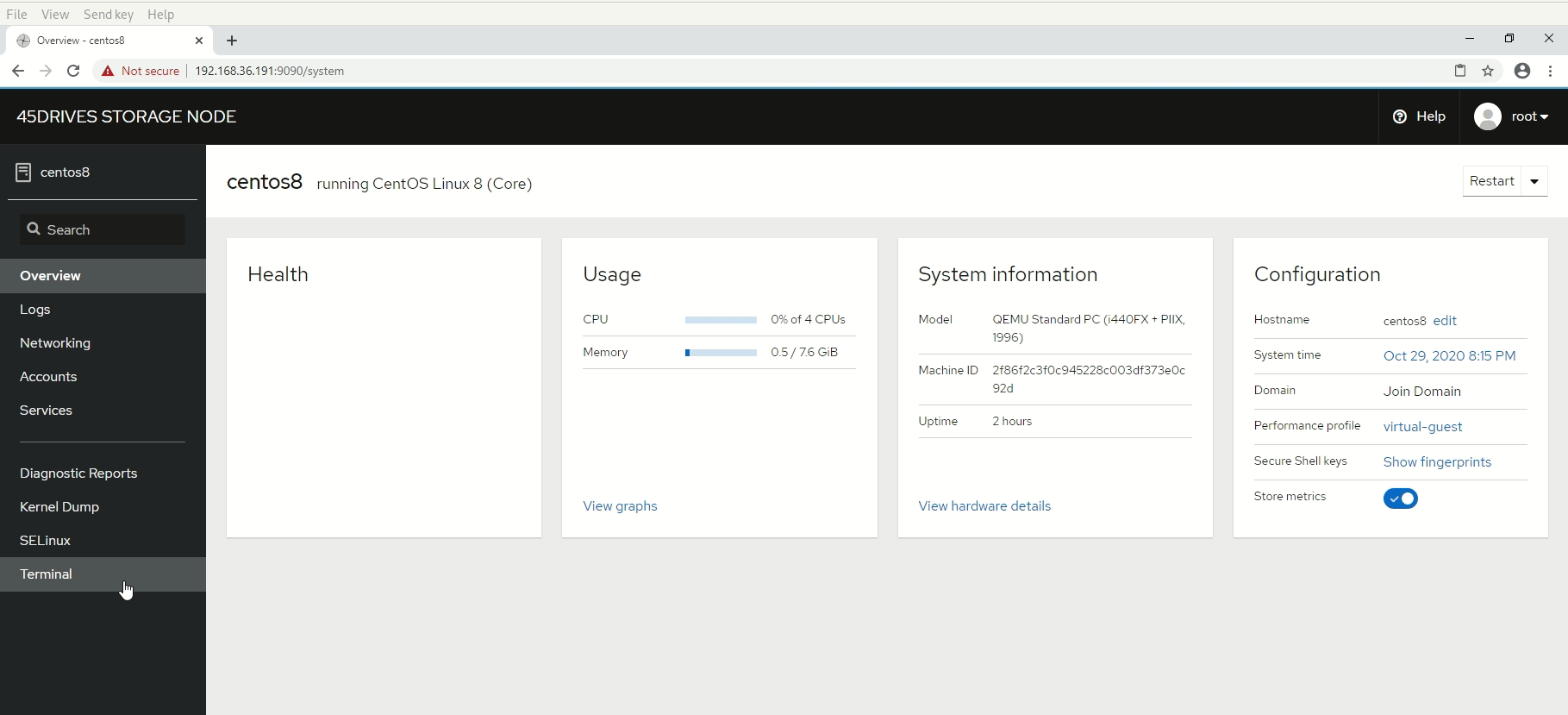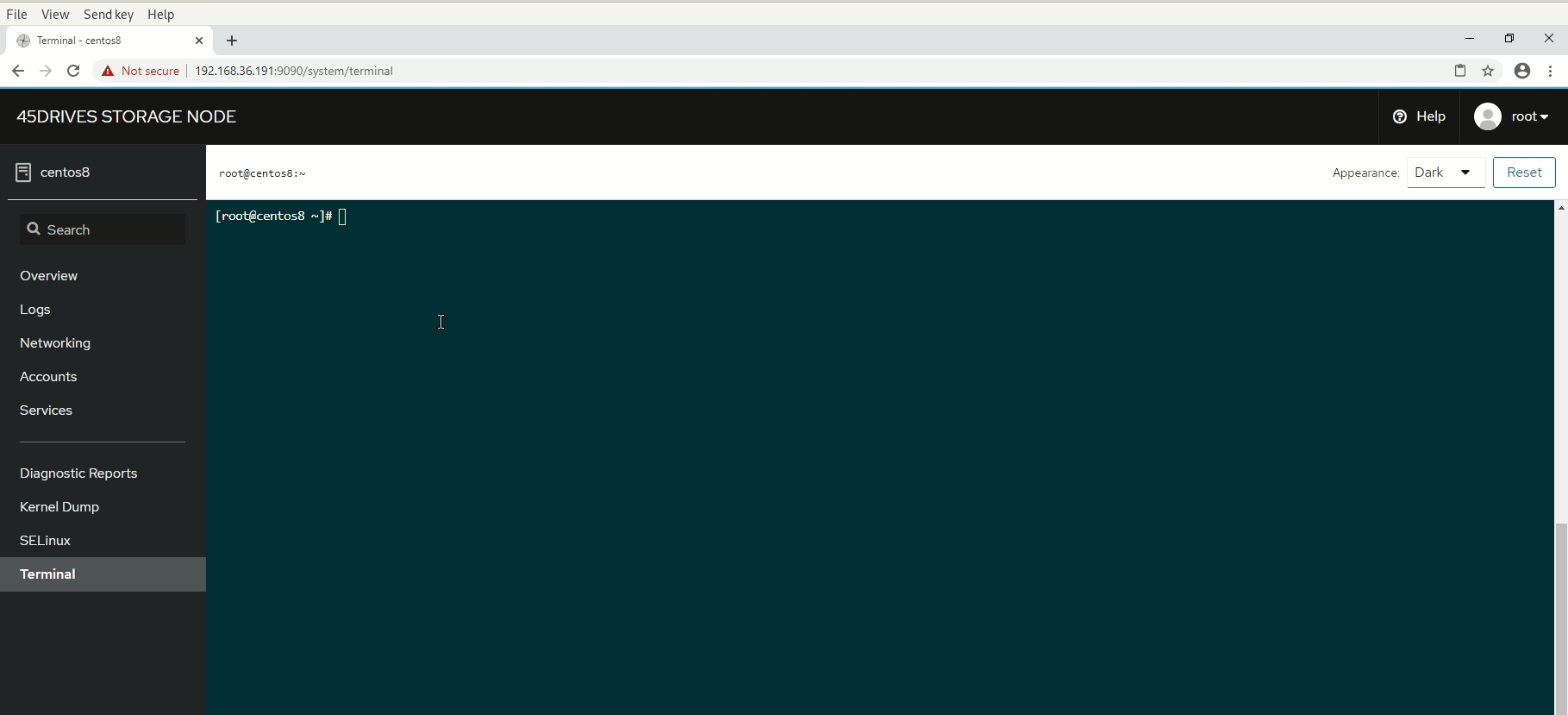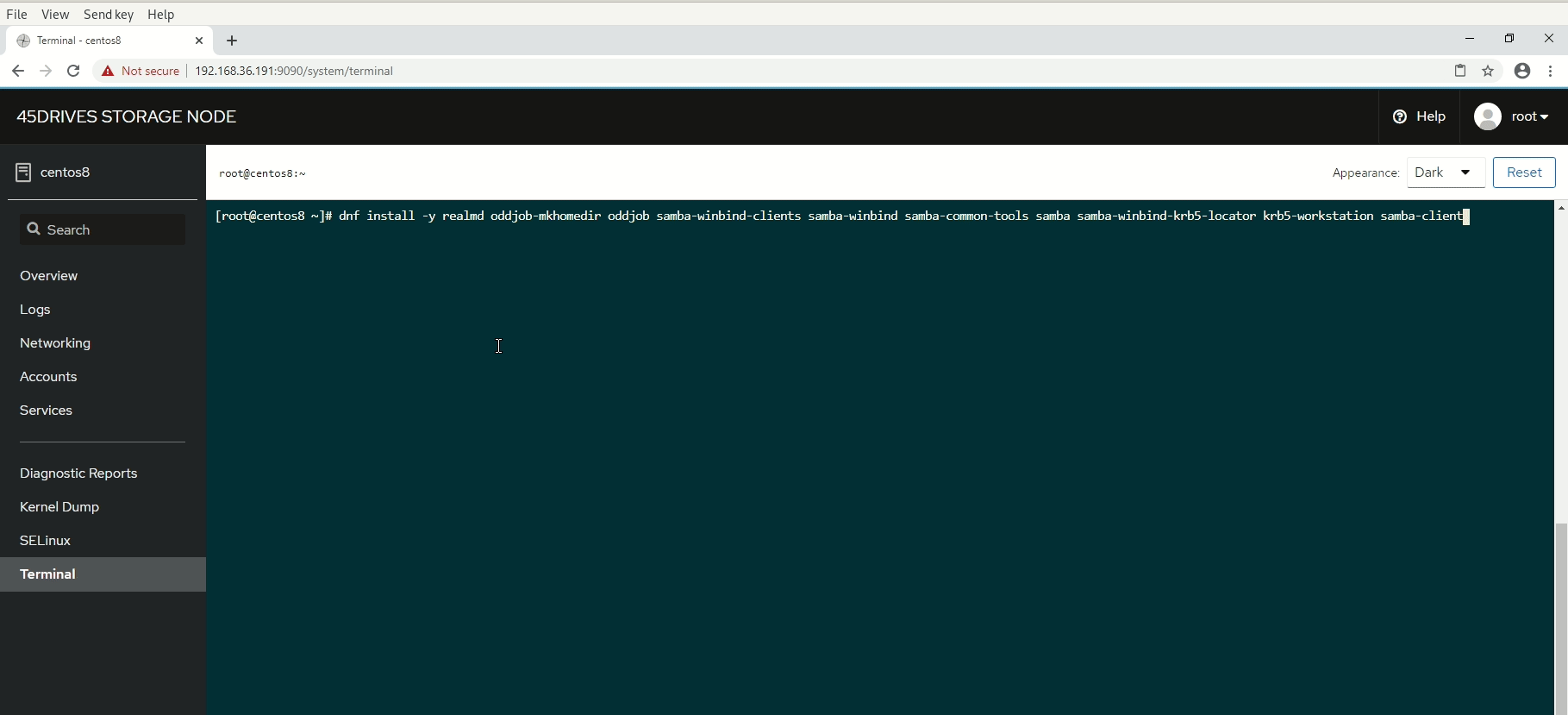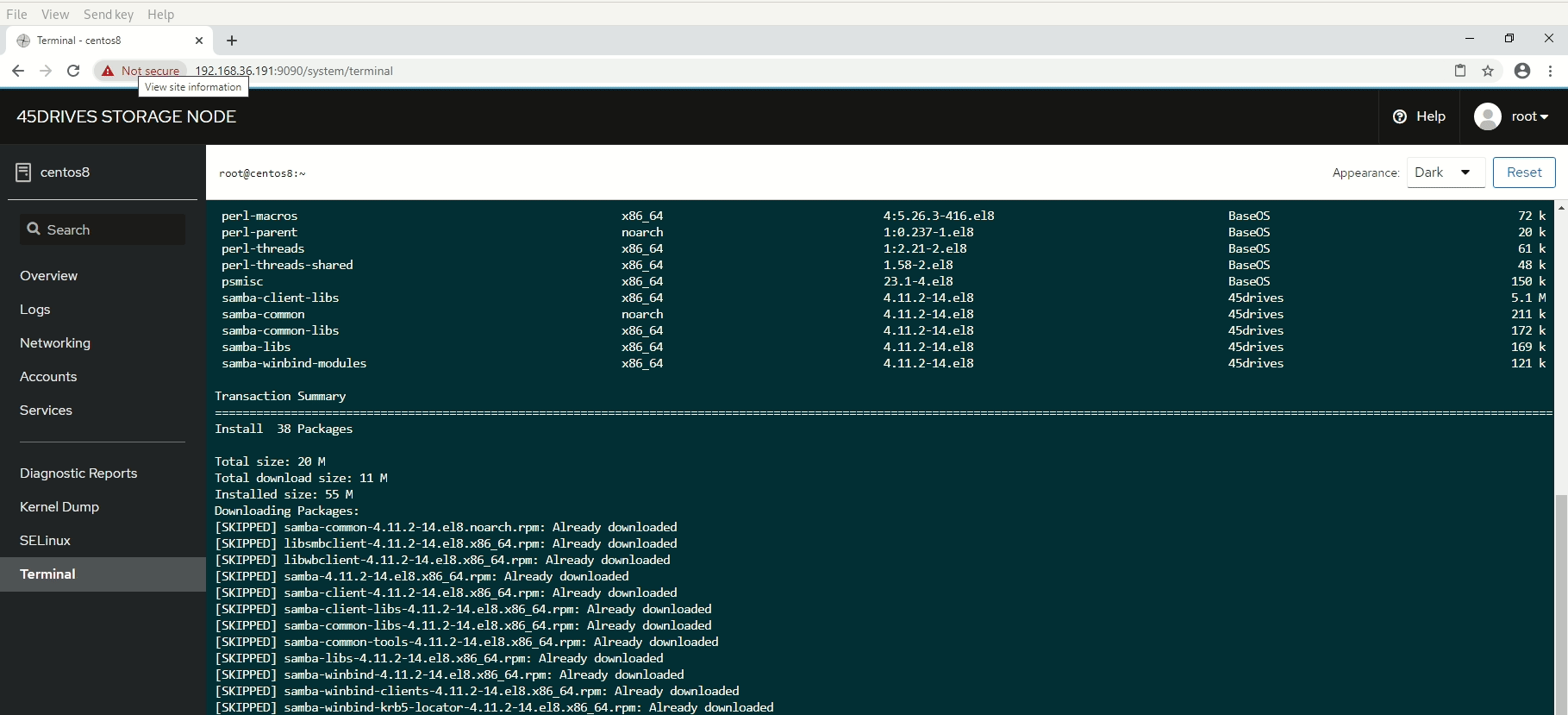
- Install packages needed for domain join
[root@rocky-45d ~]# dnf install -y realmd oddjob-mkhomedir oddjob samba-winbind-clients samba-winbind samba-common-tools samba samba-winbind-krb5-locator krb5-workstation samba-client
Configuring realmd to use winbind
- Set domain-client to winbind instead of sssd
[root@rocky-45d ~]#sed -i 's/^\(default-client = \).*$/\1winbind/' /usr/lib/realmd/realmd-defaults.conf
- Then restart the realmd service.
Configuring Hostname and DNS
- Set hostname to include domain name if not set already, this is done in the Overview tab of the Houston UI.
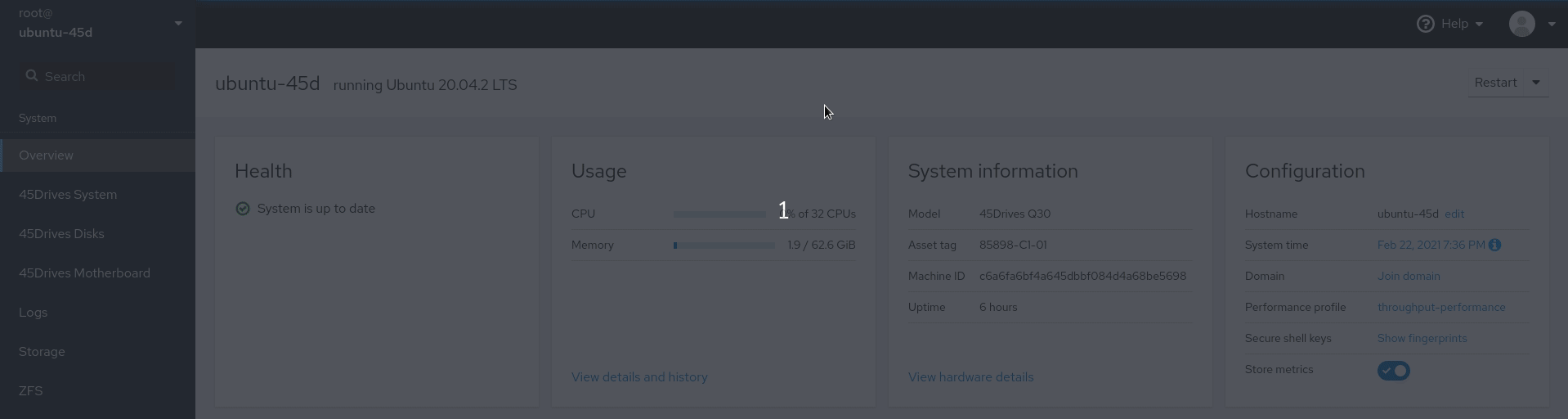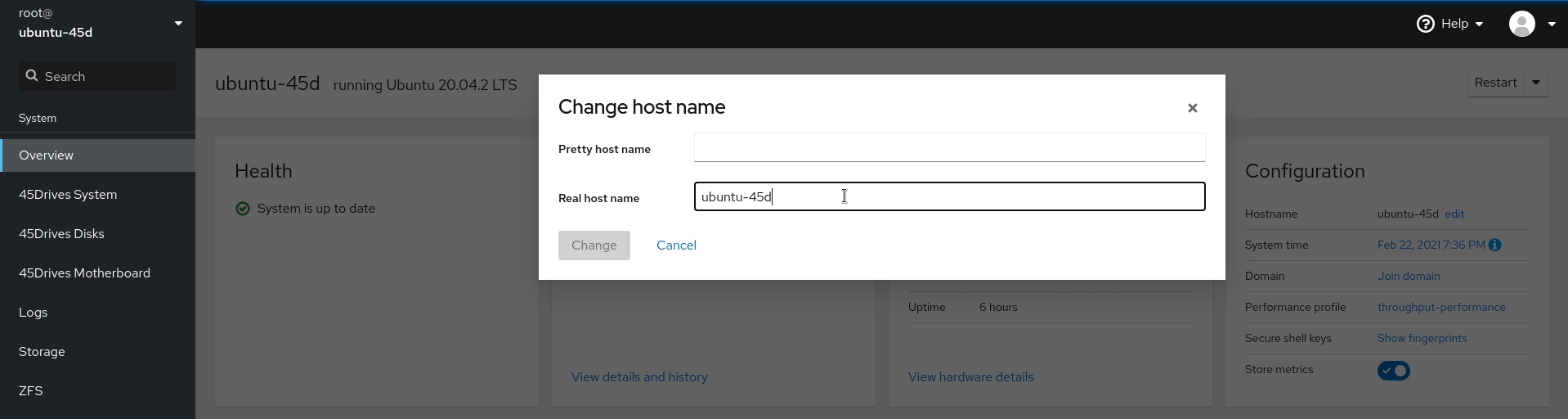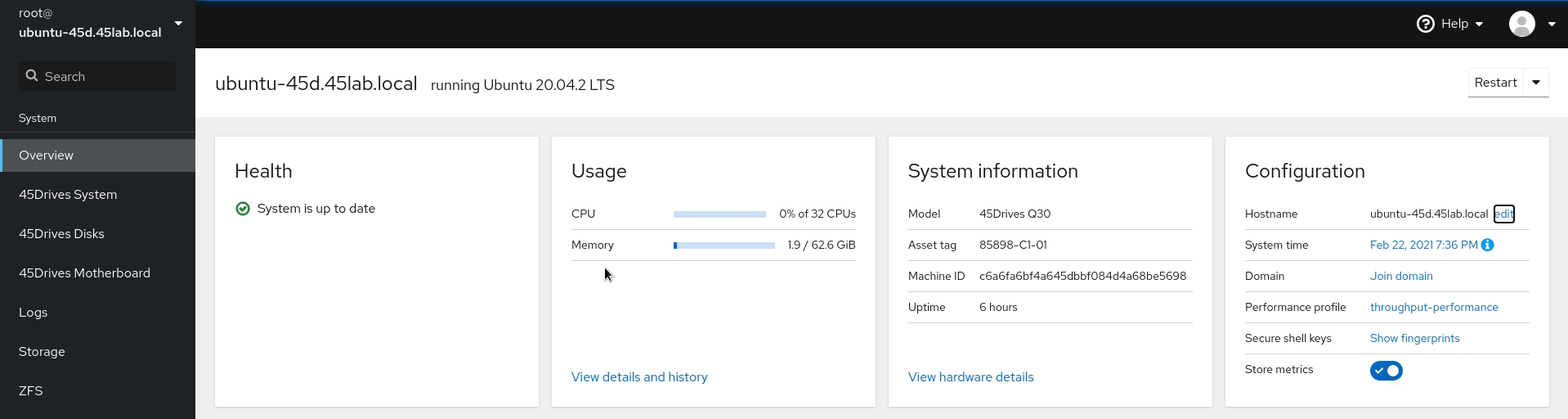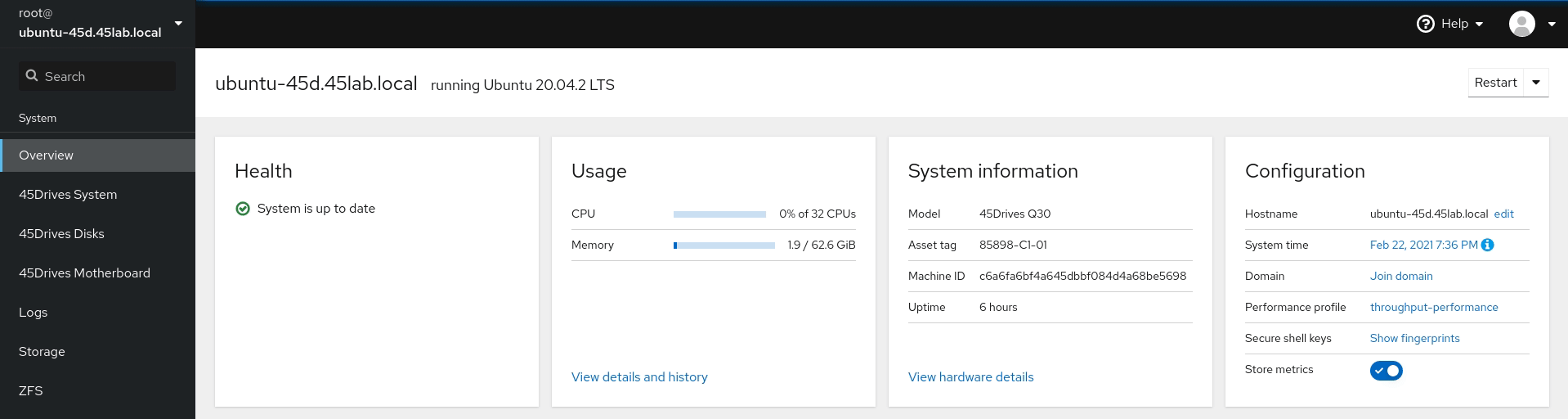
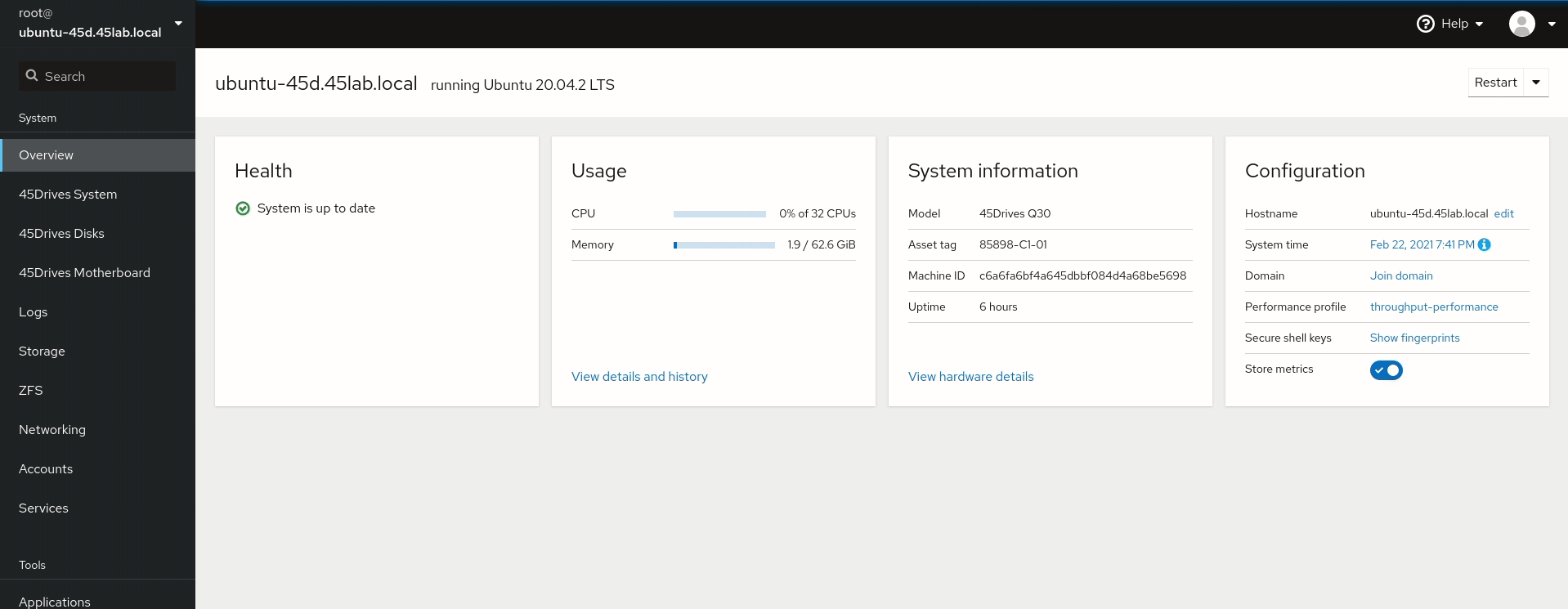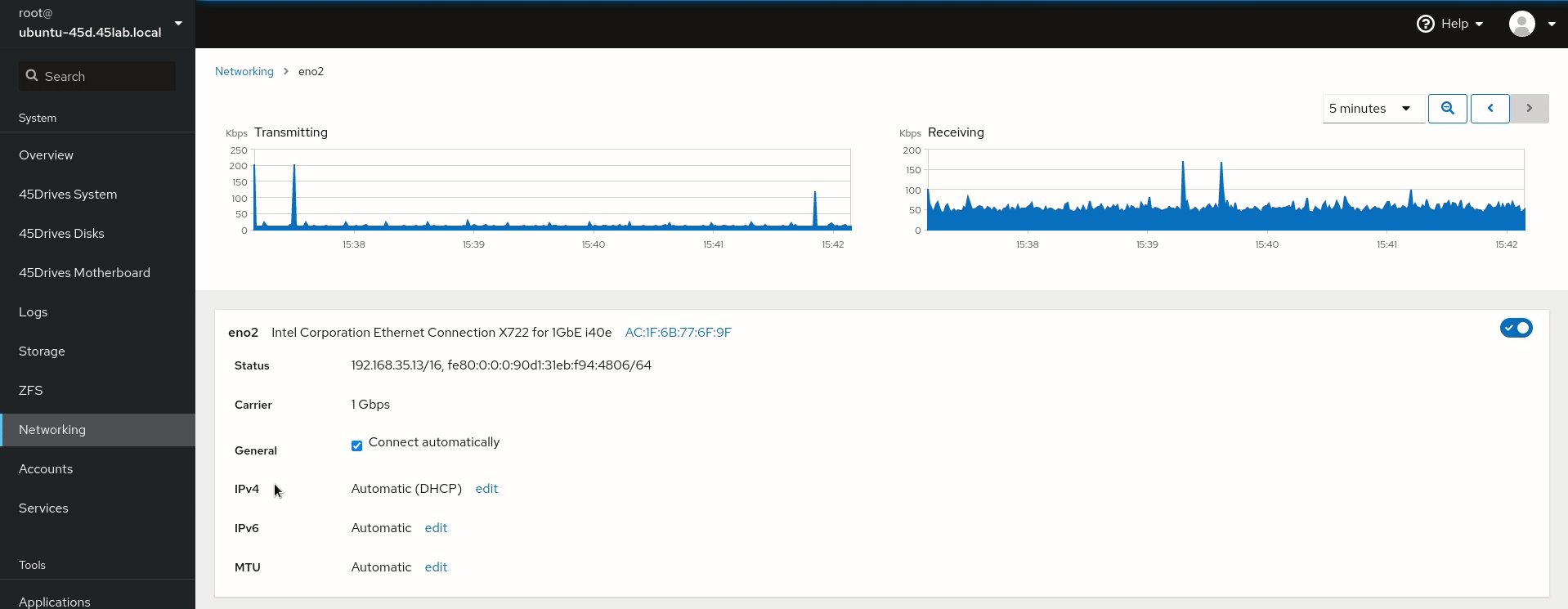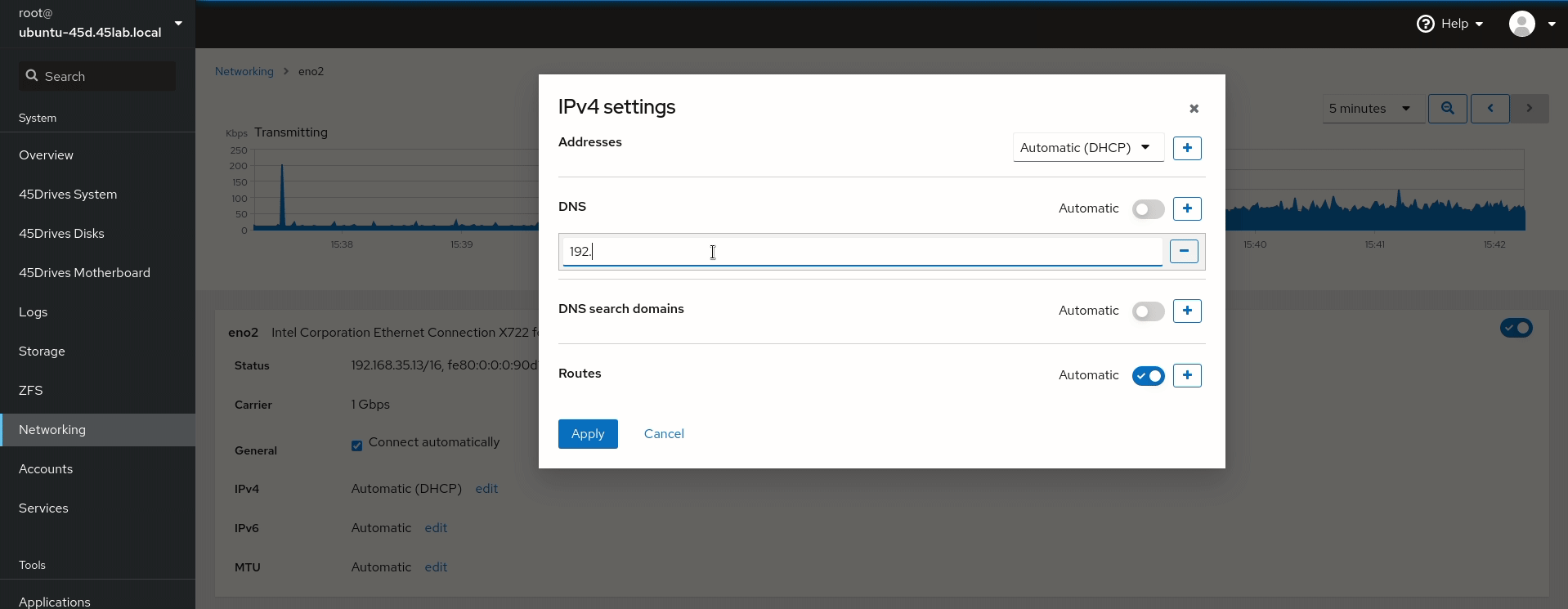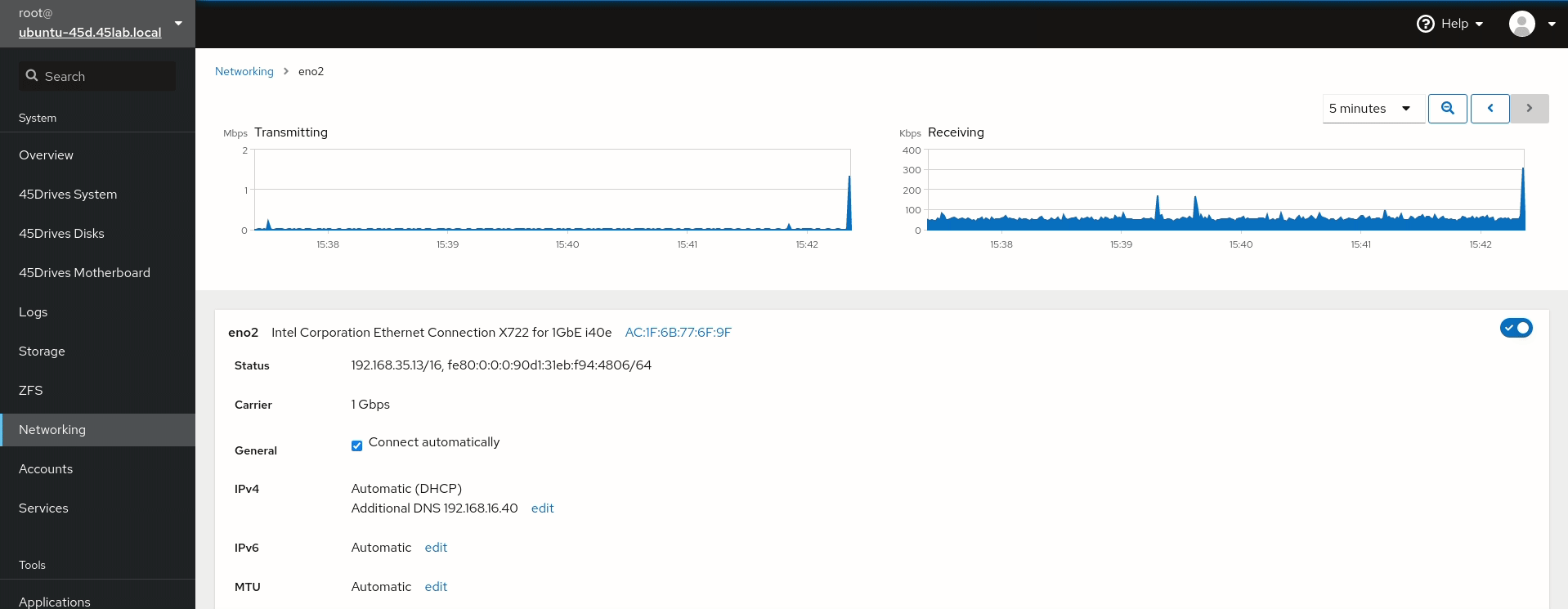
- Set DNS server to the IP of the Domain Controller if not done already. This is done in the network tab of the Houston UI
Joining the Domain
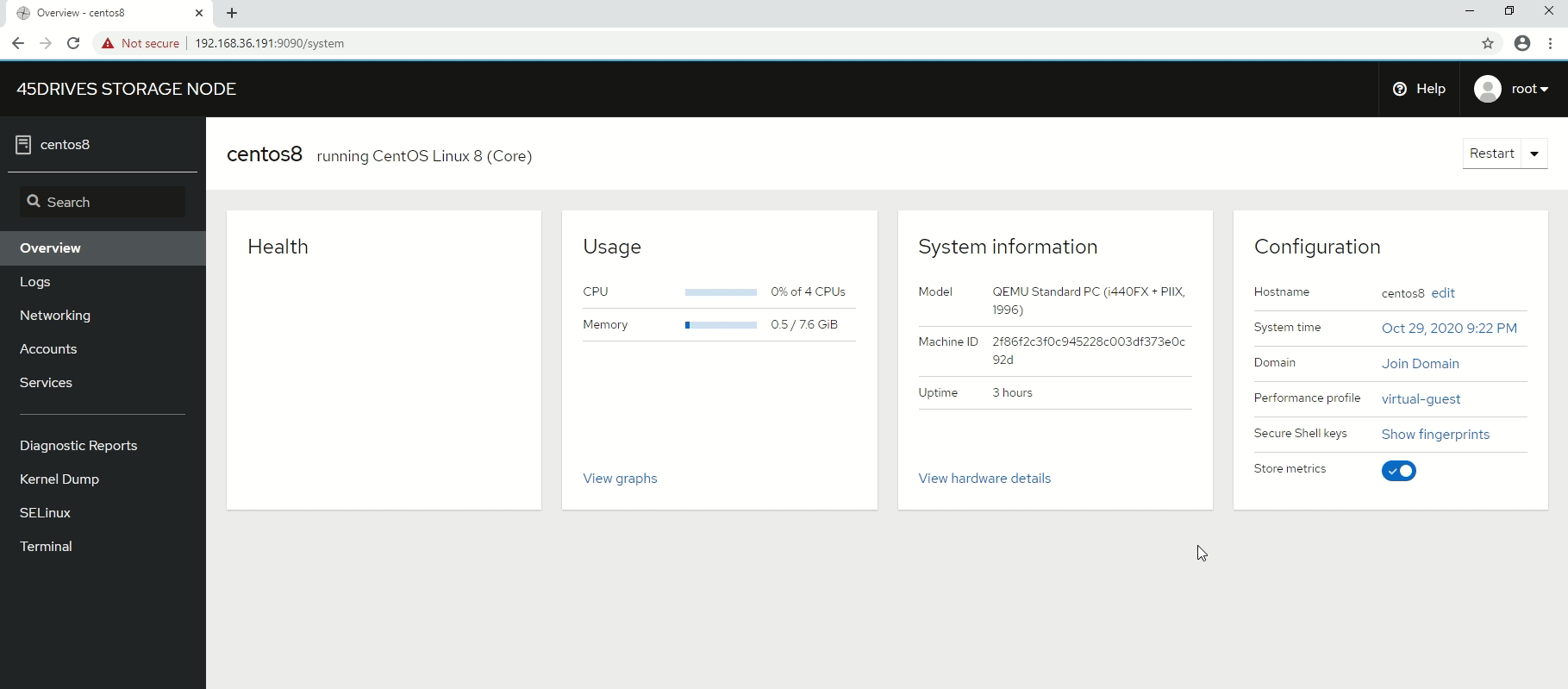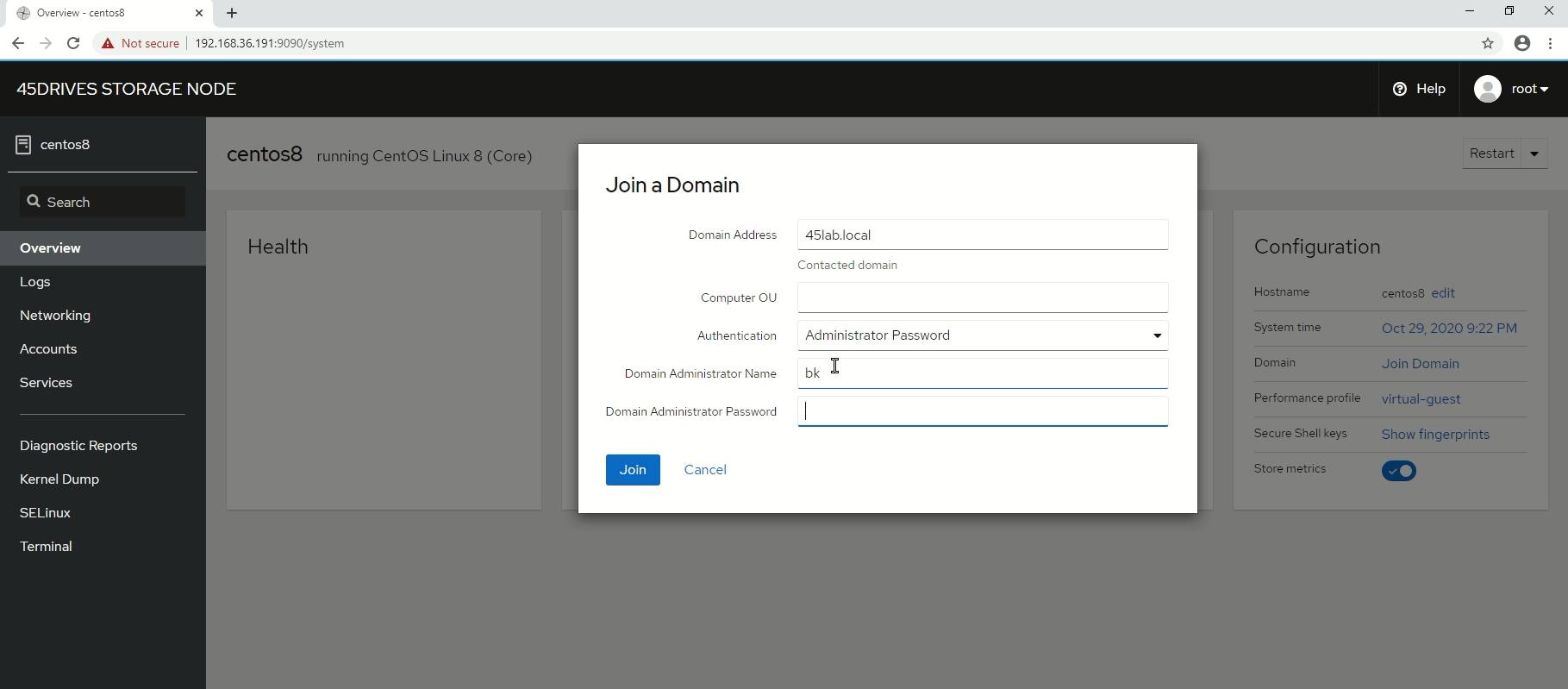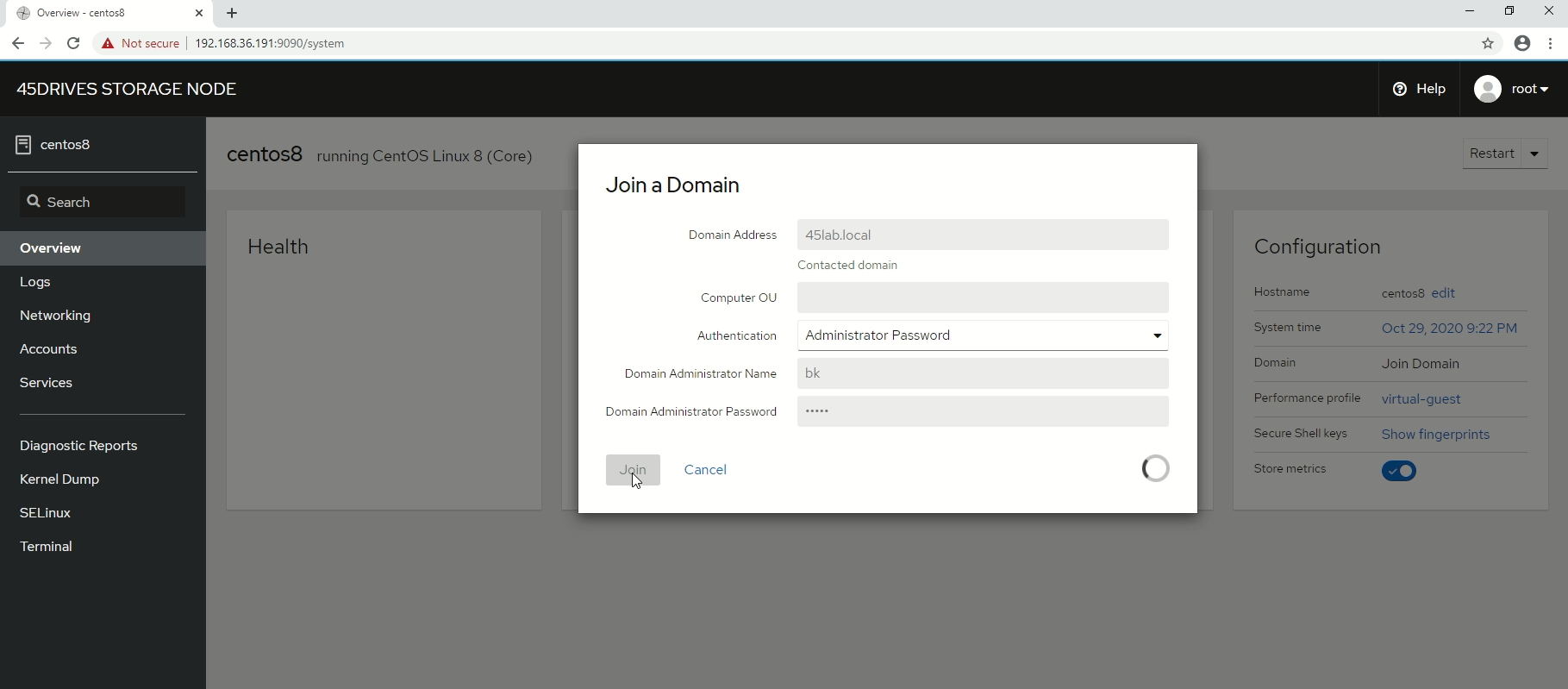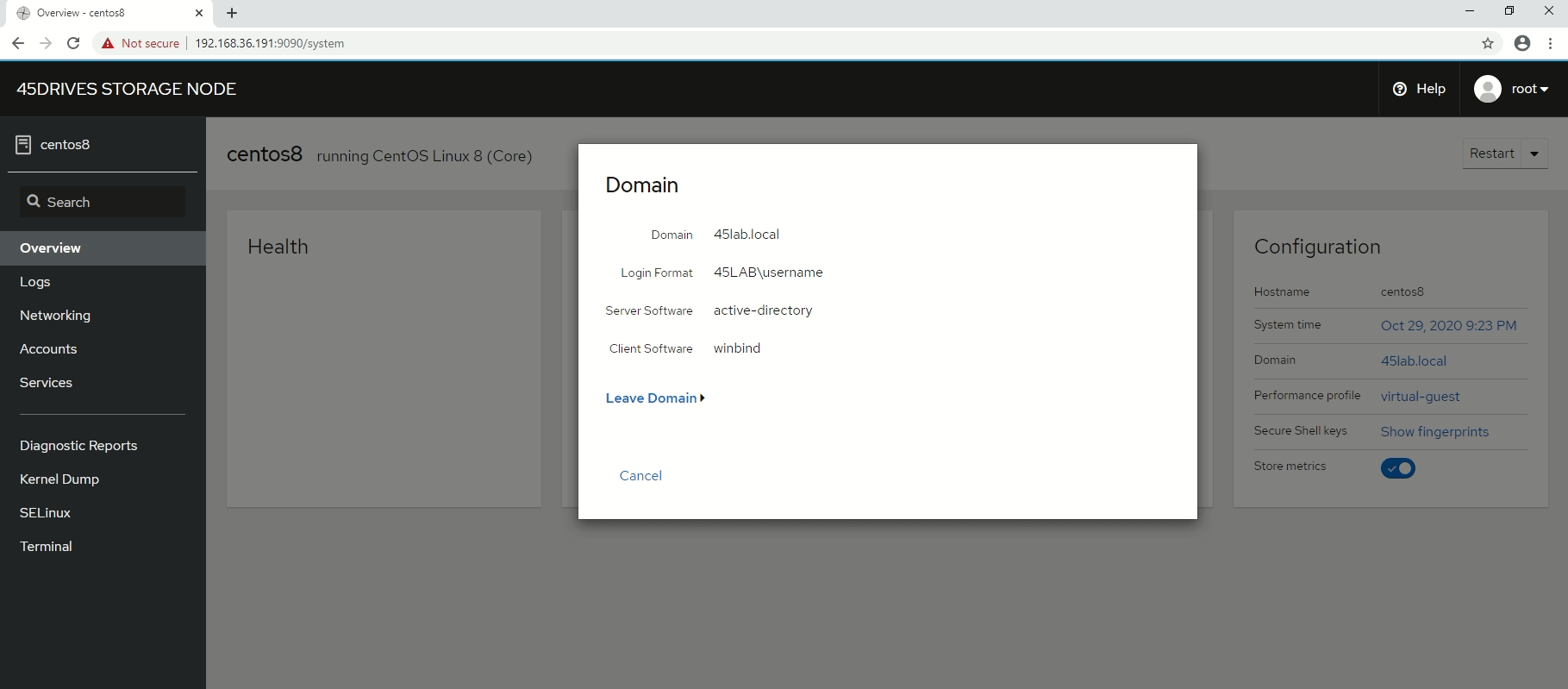
- Join Domain, refresh the page if the Join Domain button is greyed out
Granting SeDiskOperatorPrivilege
- Now we need to grant the SeDiskOperatorPrivilege privilege to any domain groups / users that are going to be configuring share permissions.
[root@rocky-45d ~]# net rpc rights grant "45LAB\domain admins" SeDiskOperatorPrivilege -U "45LAB\bk" Enter 45LAB\bk's password: Successfully granted rights.
- You can list all users and groups who have this privilege by running:
[root@rocky-45d ~]# net rpc rights list privileges SeDiskOperatorPrivilege -U "45LAB\bk" Enter 45LAB\bk's password: SeDiskOperatorPrivilege: SeDiskOperatorPrivilege: BUILTIN\Administrators 45LAB\domain admins
If this is not done, then we cannot set the initial group ownership to configure permissions on any SMB shares.
Verification
- We can now communicate with our Active Directory server, and assign permissions based on the users and groups from our Active Directory.
Troubleshooting
- Ensure you have configured the server hostname and DNS address correctly.
- Ensure you have configured nsswitch.conf correctly.
-
sed -i 's/^\(passwd:\s\+files\) \(systemd\).*$/\1 winbind \2/g;s/^\(group:\s\+files\) \(systemd\).*$/\1 winbind \2/g' /etc/nsswitch.conf
-
- If net rpc rights grant is causing issues, try using net sam rights grant instead.
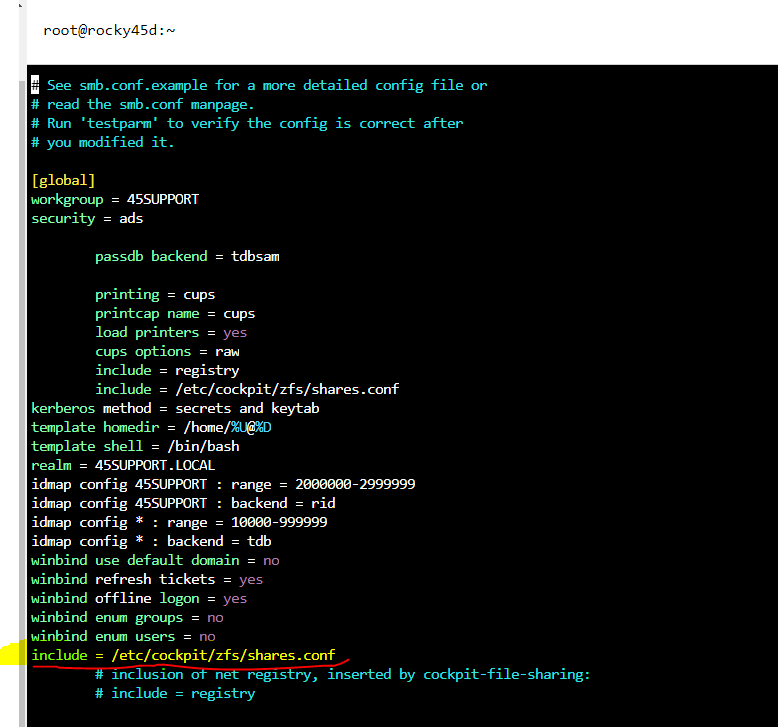
- Ensure the line “include = /etc/cockpit/zfs/shares.conf” line is at the bottom of the [global] section of the smb.conf file.
Views: 2370