Scope/Description
- This article will show how to configure SMB shares to allow access via Windows Domain Authentication and handle permissions via Windows ACLs.
Prerequisites
- SMB Packages Installed
- SMB Services Running and Enabled
- SMB Ports Open on Firewall (133/tcp, 445/tcp and 137/udp, 138/udp)
- Joined to an Active Directory if using Windows ACLs to manage share permissions.
- Domain Group(s) that will handle assigning share permissions via Windows ACLs given SeDiskOperatorPrivilege permission.
Steps
Domain Authentication Access Share
- For a basic Domain Authentication Access share, we must first ensure the permissions are set correctly on the directory we are sharing out.
- The directory must be set to 770 by doing chmod 770 /path/to/share for permissions, and the owner user/group is set as root:DOMAIN\Domain Group by doing chown root:DOMAIN\Domain Group where Domain Group is an Active Directory group that will handle the assigning of permissions via Windows ACLs.
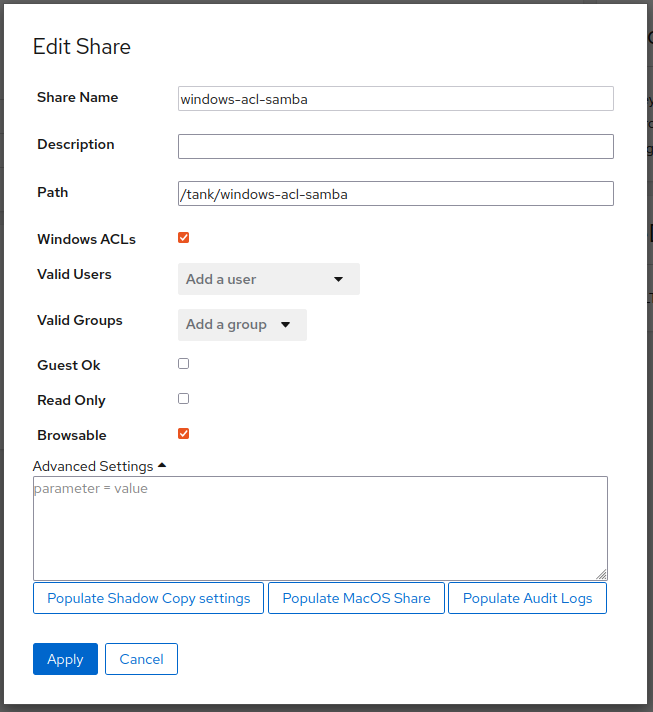
- Once we have this completed, we can then utilize a share configuration similar to below to allow access, and assigning of permissions on the share through the use of Windows ACLs.
- Note that selecting the Windows ACLs option within the File Sharing module adds the vfs objects and other parameters to the share automatically.
- To ensure full use of Windows ACLs, ensure the owner group is given the SeDiskOperatorPrivilege so they can then modify and manage the SMB share permissions using Windows ACLs.
[samba-windows-acls] map acl inherit = Yes path = /tank/samba-windows-acls read only = No vfs objects = acl_xattr acl_xattr:ignore system acl = yes
Verification
- We can now access our SMB shares using our Windows Active Directory Domain Credentials.
Troubleshooting
- Ensure there are no typos within your share configuration parameters.
- Ensure your system is already joined to your Windows Active Directory.
Further Reading
Views: 5064