Scope/Description
- This article will walk through the process of joining a Windows Active Directory through the Houston UI with Ubuntu 20.04.
Prerequisites
- Ubuntu 20.04 LTS installed
- Cockpit 237.1 or greater installed
- Samba, Winbind, and Realmd packages installed
- 45Drives Repository installed
Steps
Installing realmd
- Install realmd (0.16.3-3ubuntu2) from 45Drives Repository
root@ubuntu-45d:~# apt install realmd
Configuring realmd to use winbind
- Set realmd default client to winbind instead of sssd
root@ubuntu-45d:~# sed -i 's/^\(default-client = \).*$/\1winbind/' /usr/lib/realmd/realmd-defaults.conf root@ubuntu-45d:~# systemctl restart realmd
Configuring Hostname and DNS
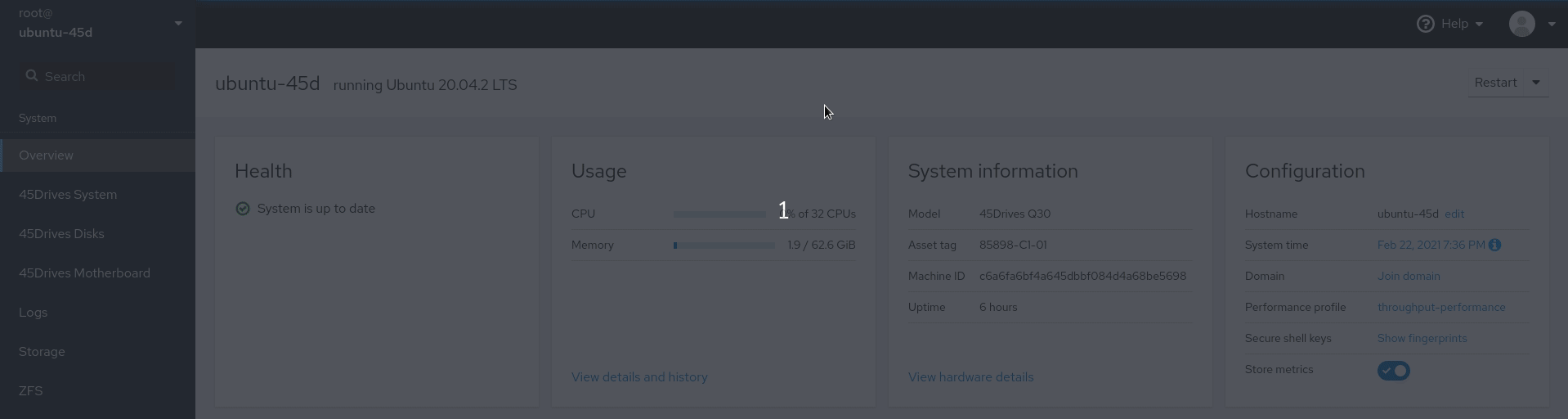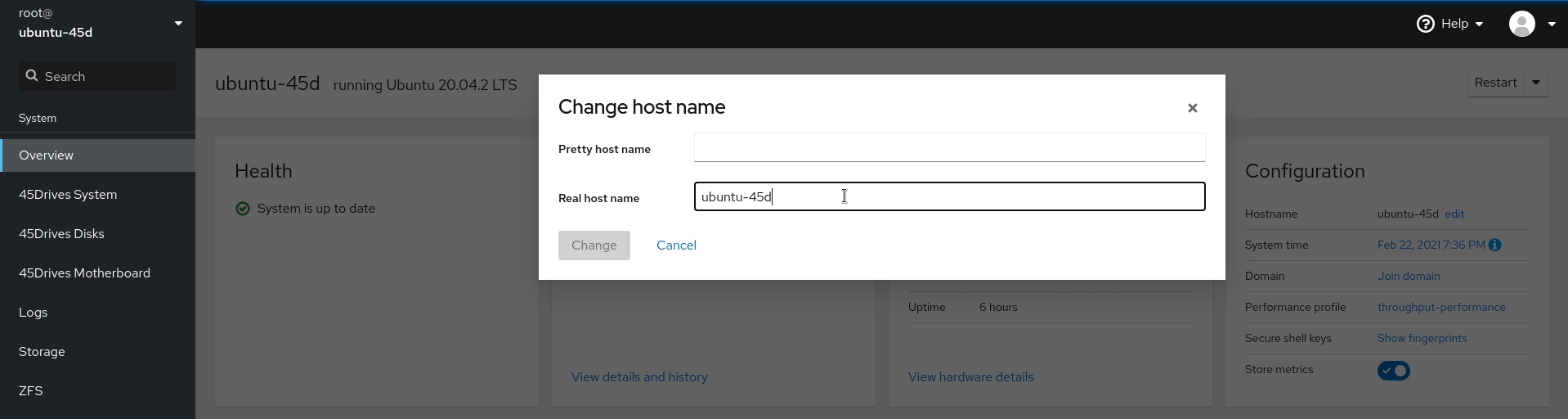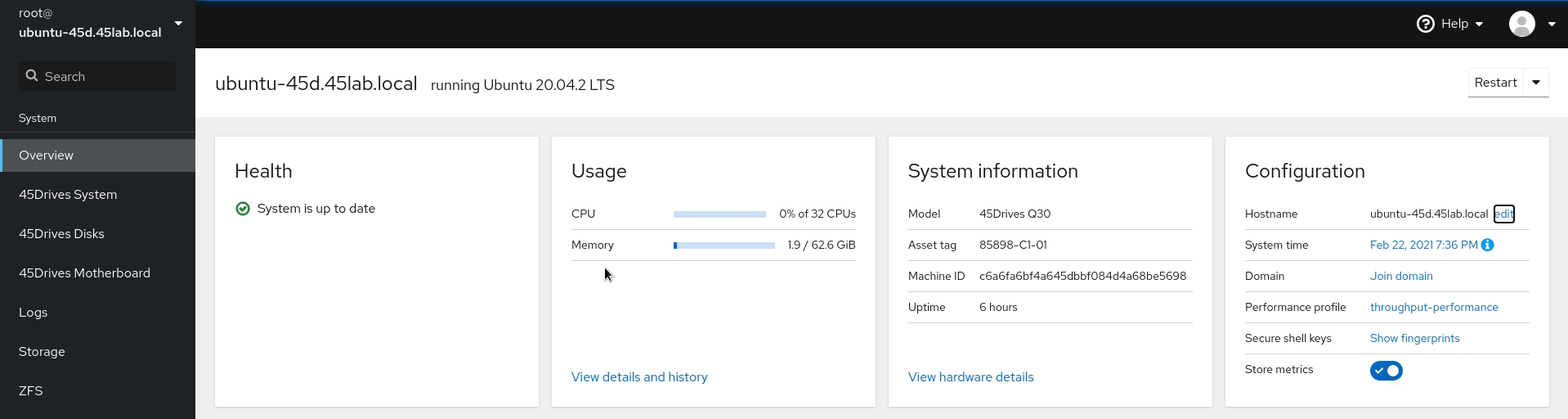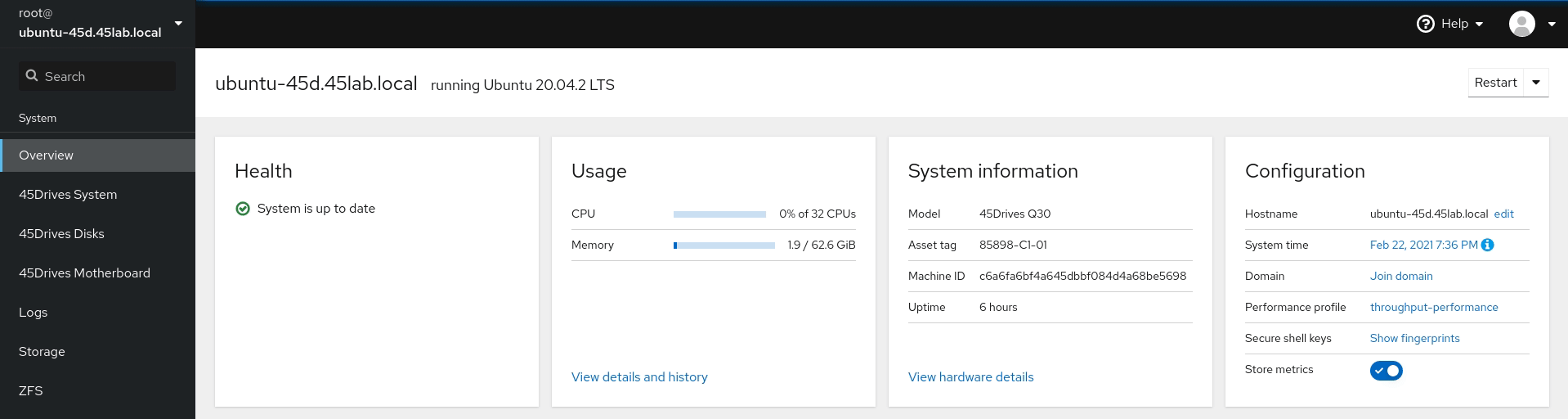
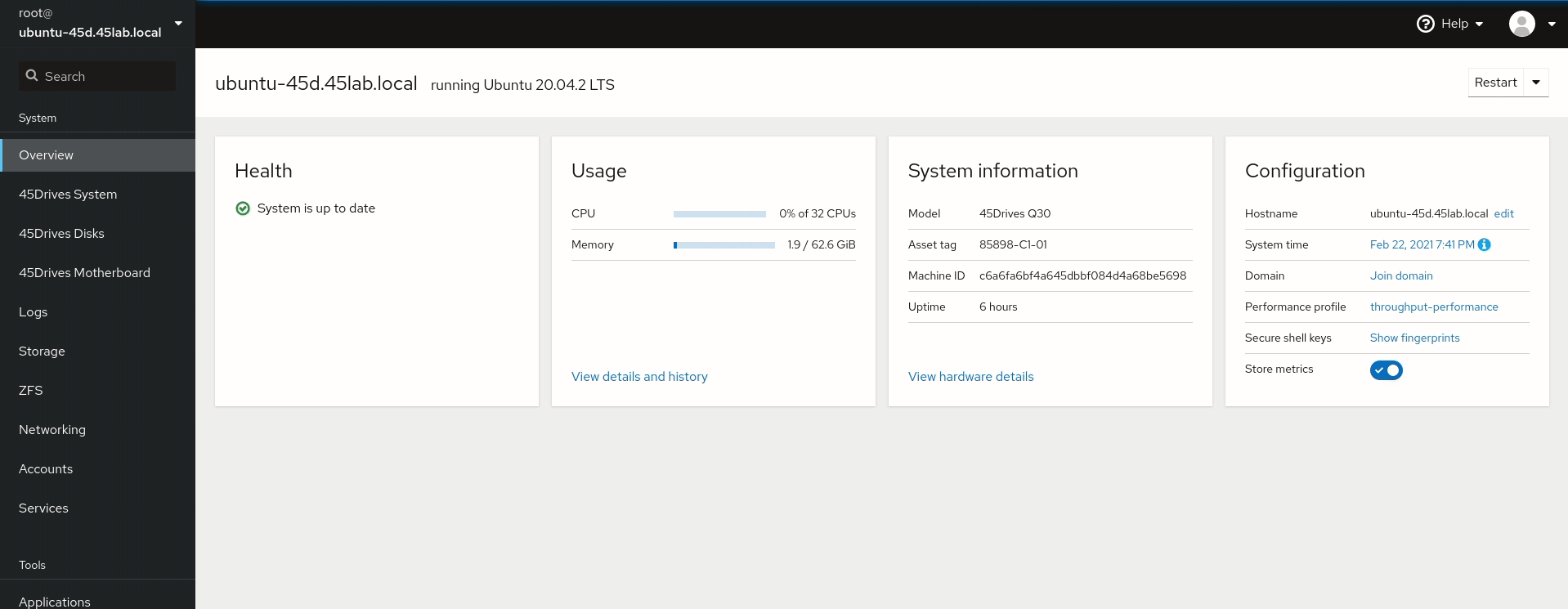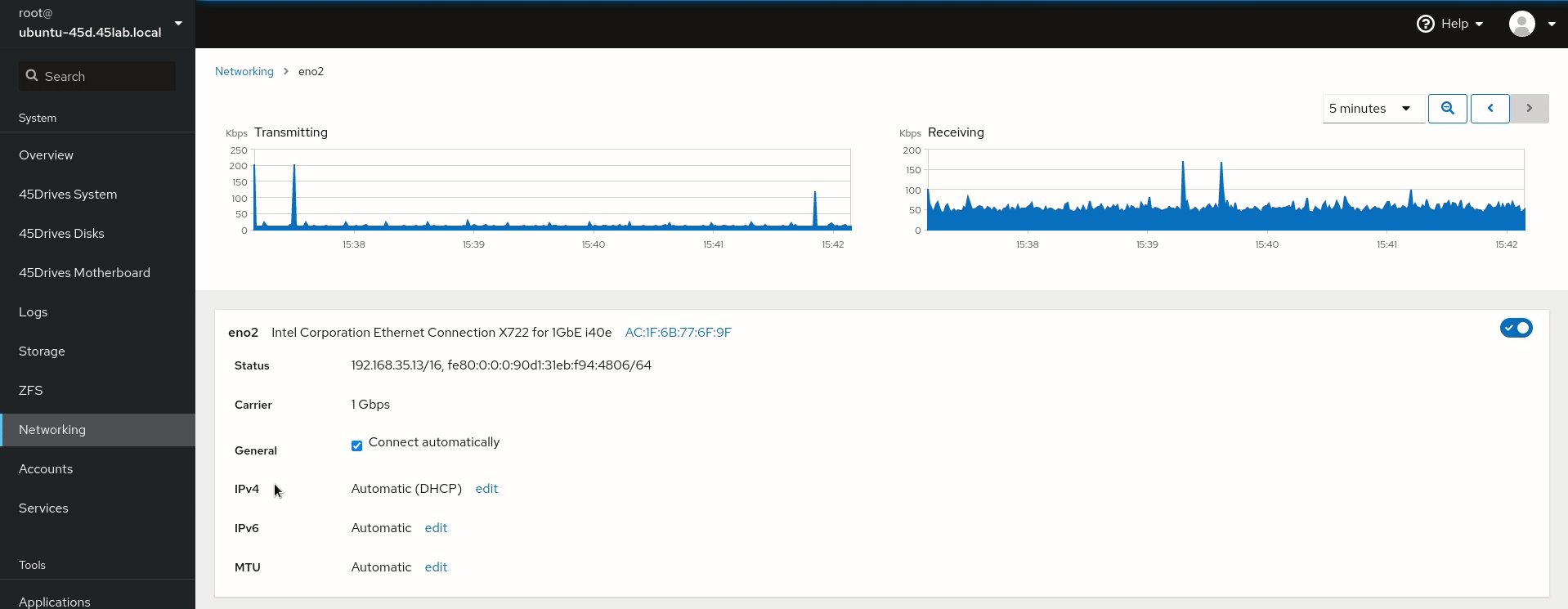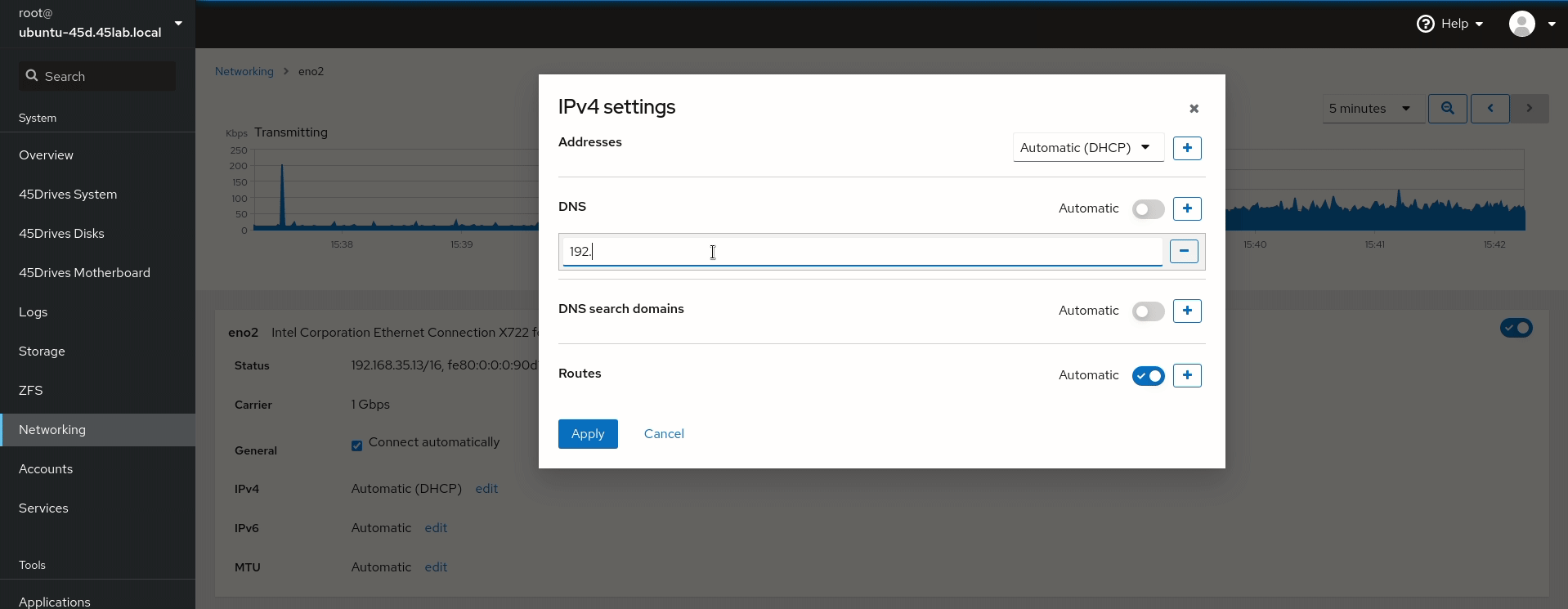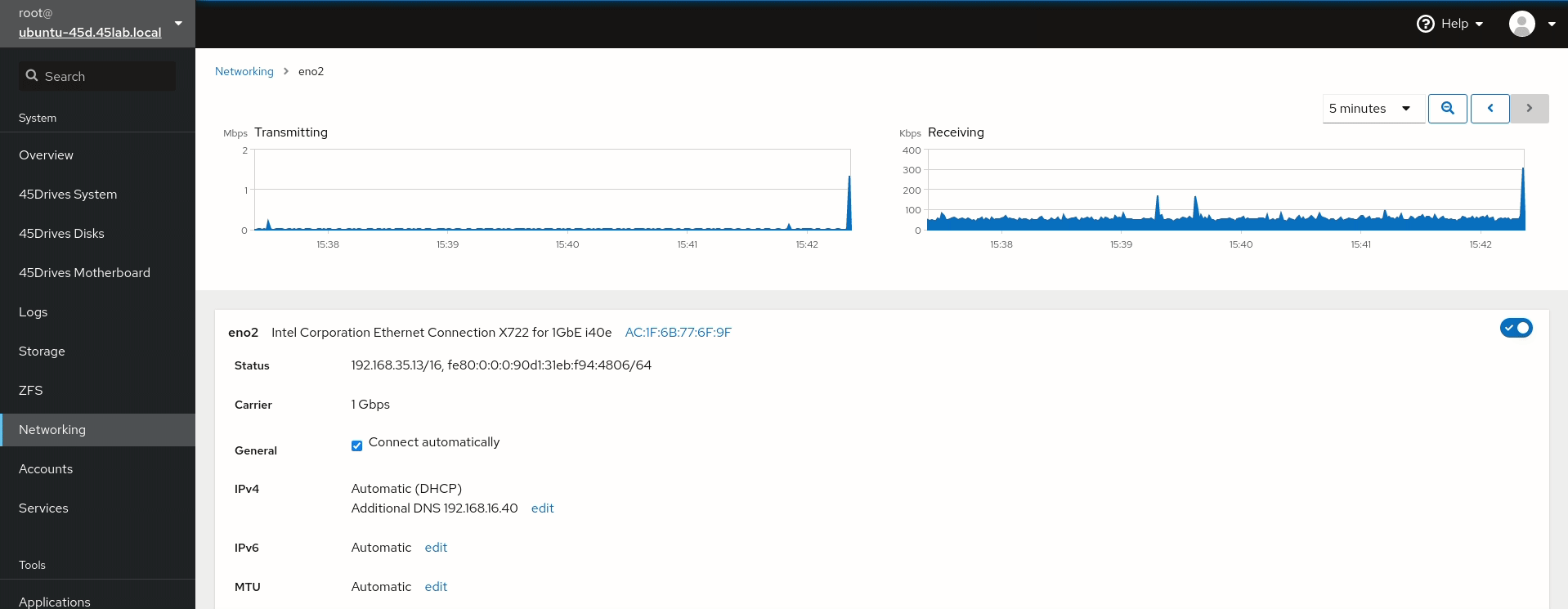
- Set hostname of the system to include domain name if not set already, this is done in the Overview tab of the Houston UI.
- Set DNS server to the IP of the Domain Controller if not done already. This is done in the network tab of the Houston UI
Generating smb.conf
- Move the existing smb.conf and keep as a backup, as realmd will autogenerate what we need to complete the join.
root@ubuntu-45d:~# mv /etc/samba/smb.conf /etc/samba/smb.conf.backup
Ensure this is done, otherwise realmd will attempt to place it’s info into the existing template smb.conf which may cause issues with the domain join.
Joining the Domain
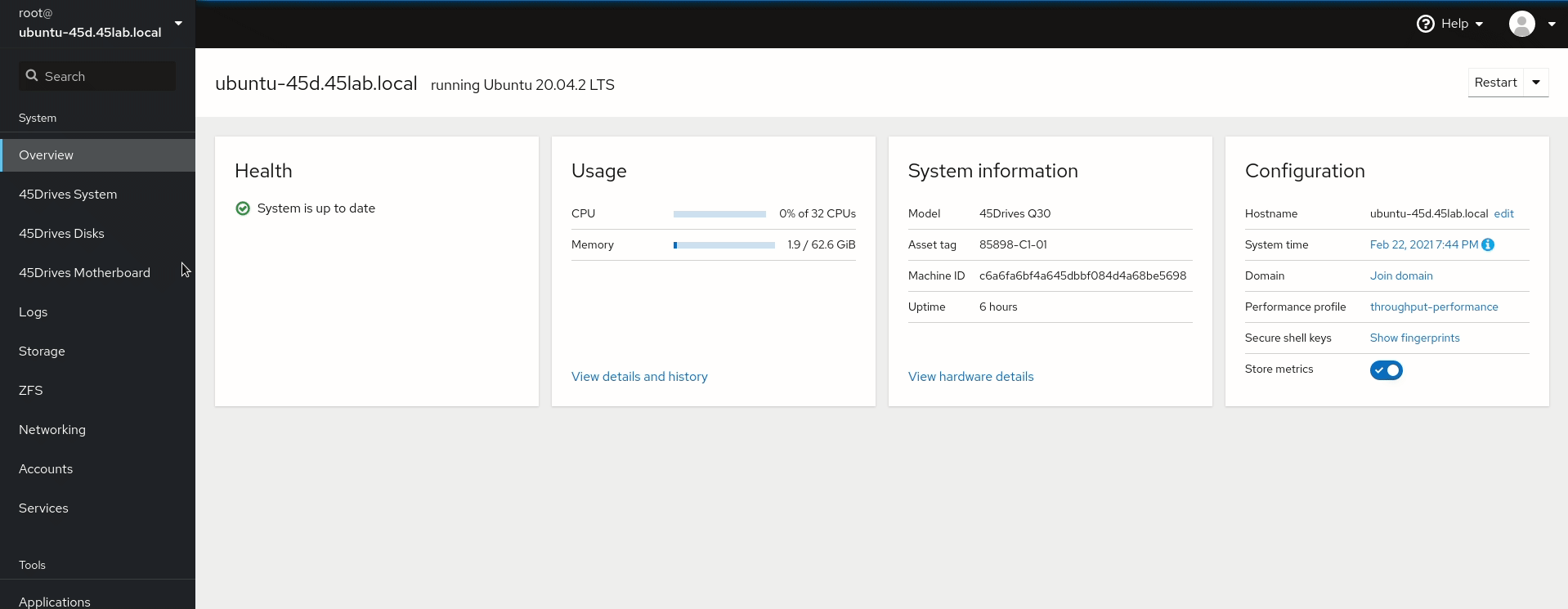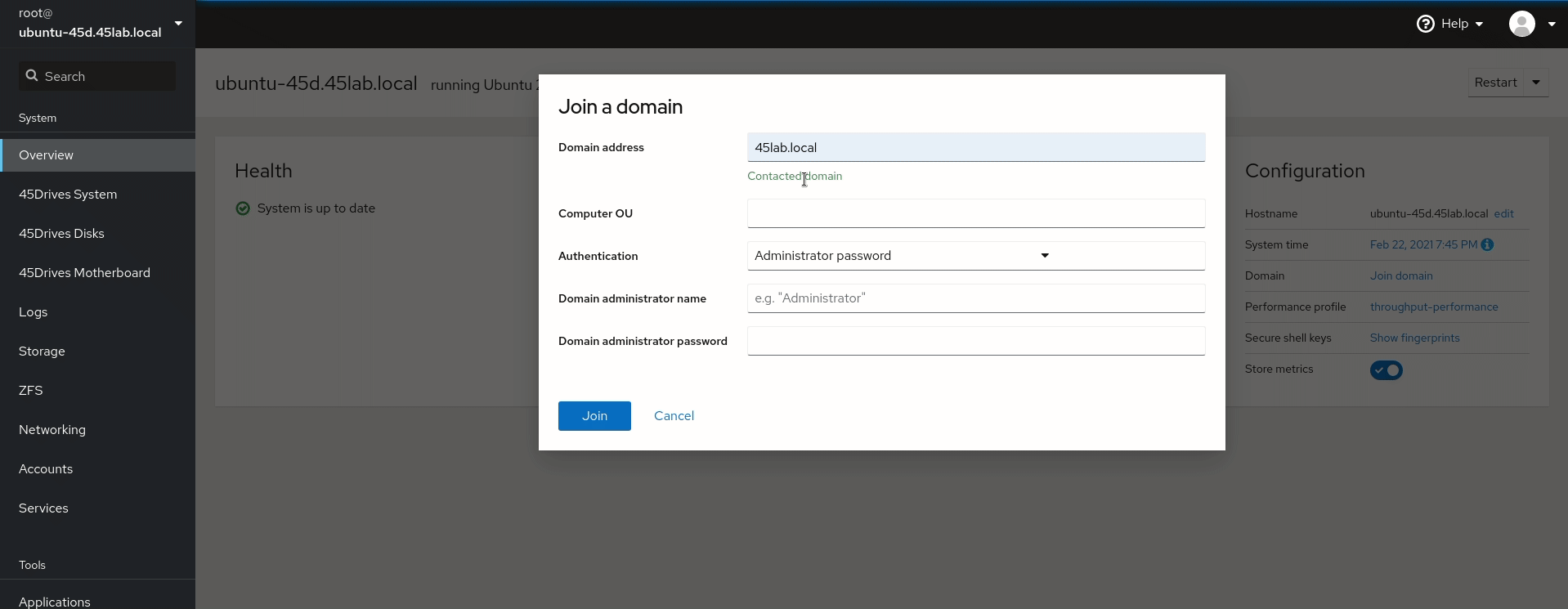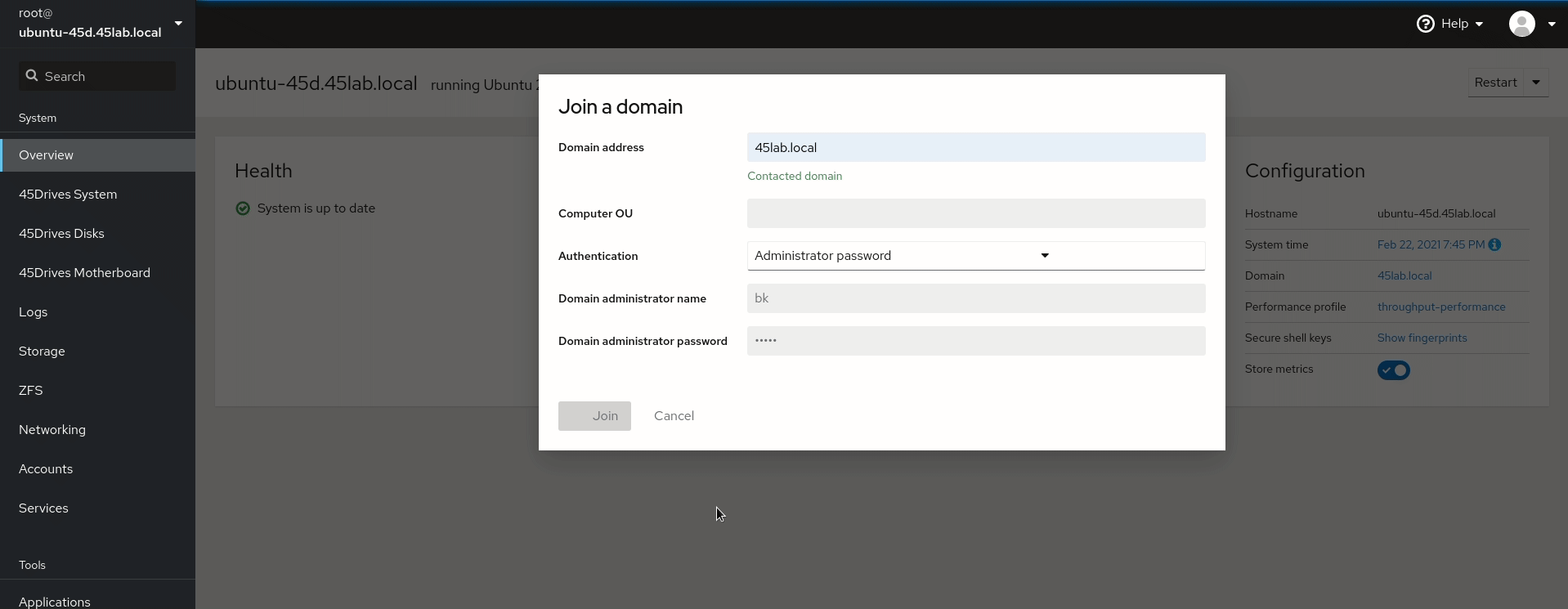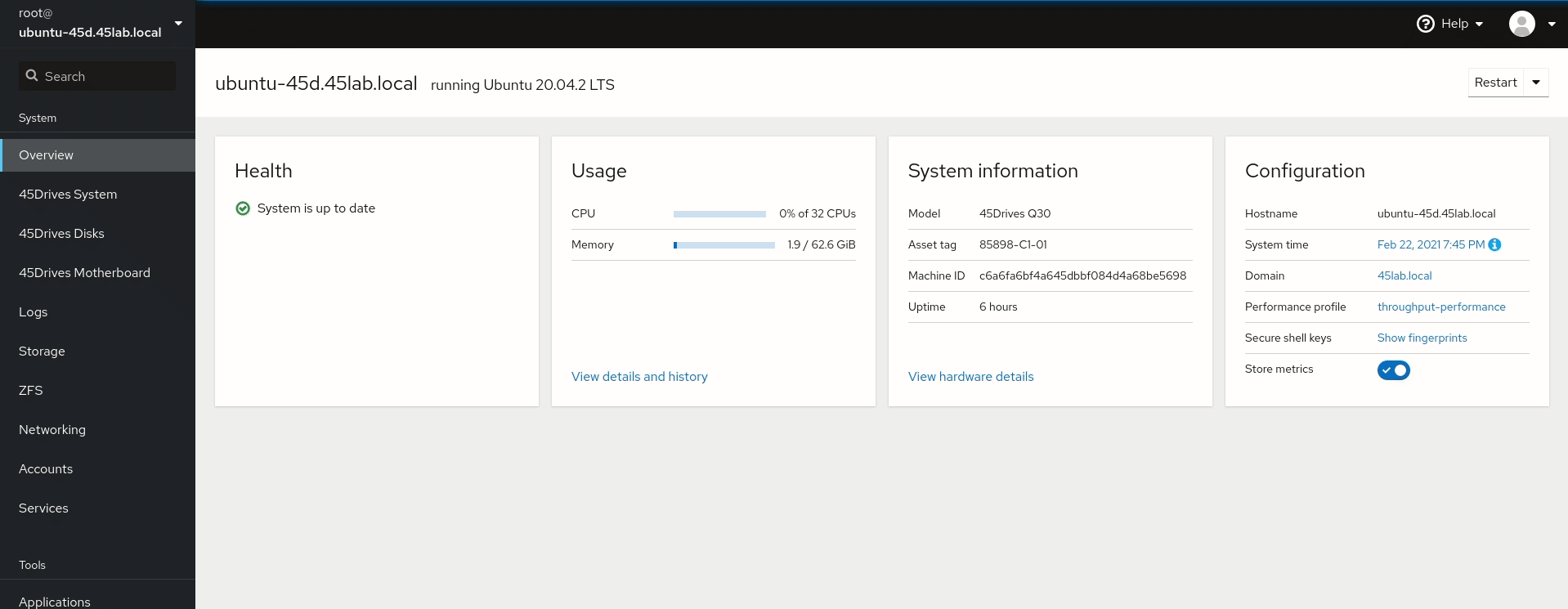
- Join the domain, this is done the Overview tab of the Houston UI. You will need the login info for user with Join Permissions to the AD.
- You will need the login info for user with Join Permissions to the AD.
- Verify after join that “winbind” was used as the client join software. If not leave the domain and return to the step “Set realmd default client to winbind instead of sssd” above.
Configuring nsswitch.conf to use winbind
- Configure nsswitch.conf.
root@ubuntu-45d:~# sed -i 's/^\(passwd:\s\+files\) \(systemd\).*$/\1 winbind \2/g;s/^\(group:\s\+files\) \(systemd\).*$/\1 winbind \2/g' /etc/nsswitch.conf
If this is not done, then we cannot set the initial group ownership to configure permissions on any SMB shares.
- Configure PAM to to enable the creation of home directories on first login for network users
root@ubuntu-45d:~# pam-auth-update --enable mkhomedir
- Verify Domain users and groups are available
- User id format is ‘DOMAIN\username’
root@ubuntu-45d:~# id '45LAB\rob' uid=2001106(45LAB\rob) gid=2000513(45LAB\domain users) groups=2000513(45LAB\domain users),2001106(45LAB\rob),2001105(45LAB\lab)
- All users in the Domain can now login into the server, this is not ideal as it is best practise to block all Domain users and let the admin decide on can get in.
- To restrict access to specific users/groups see this article
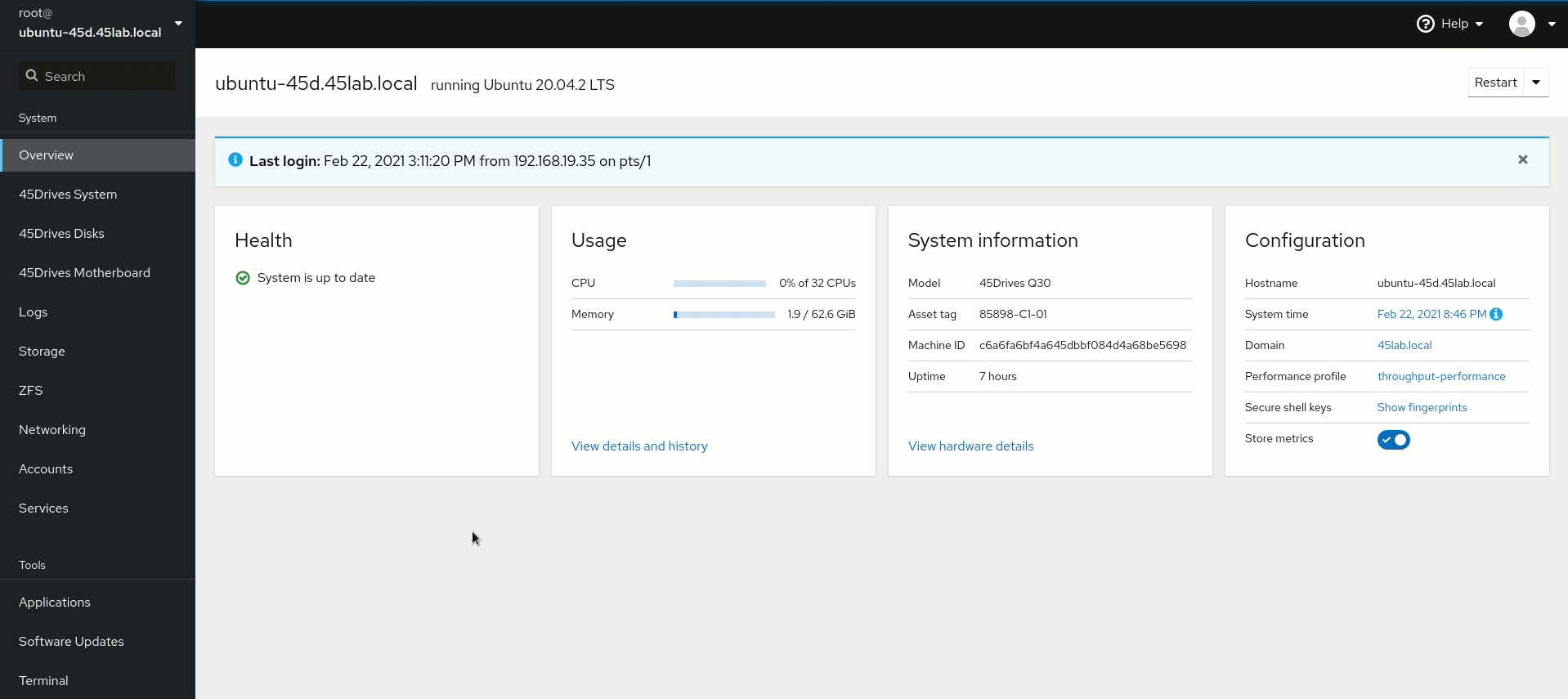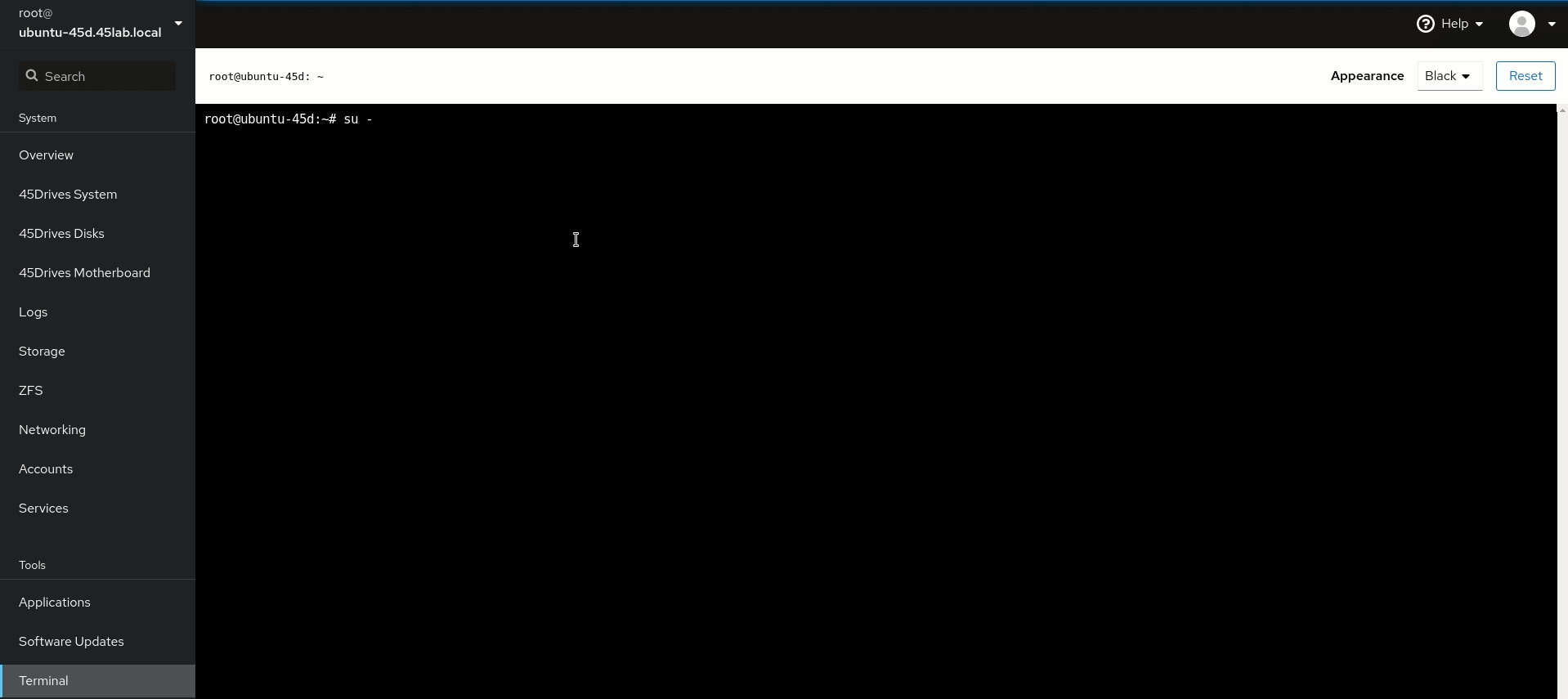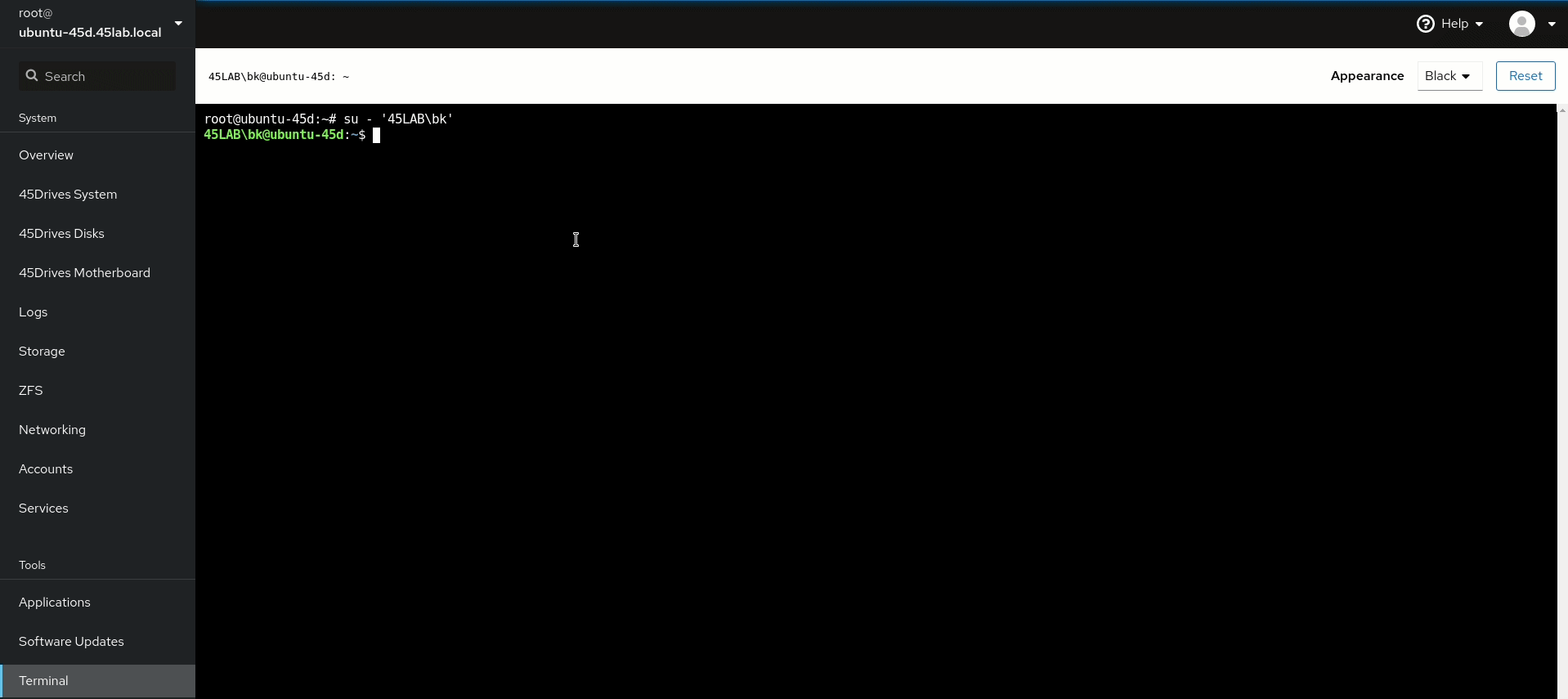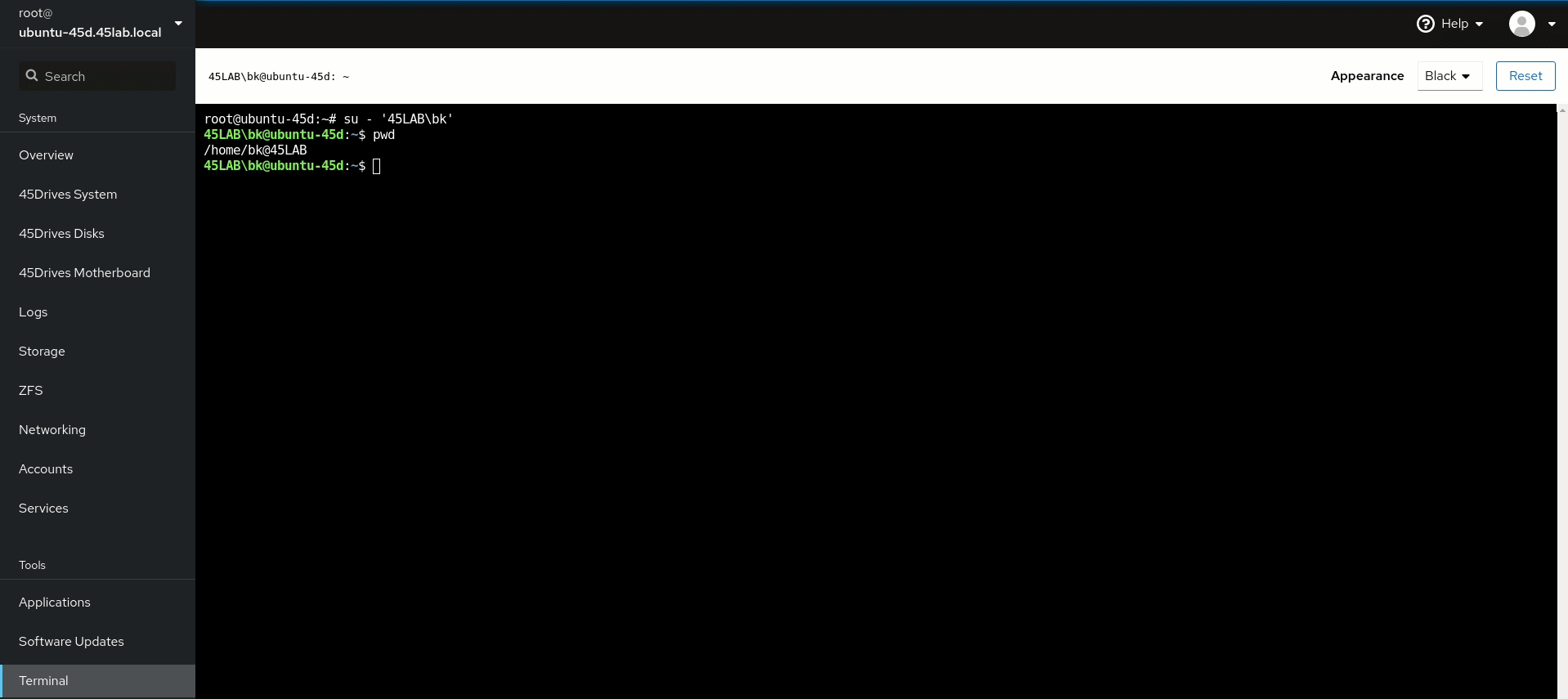
- Test login for a Domain User
Granting SeDiskOperatorPrivilege
- Now we need to grant the SeDiskOperatorPrivilege privilege to any domain groups / users that are going to be configuring share permissions.
[root@ubuntu-45d ~]# net rpc rights grant "45LAB\domain admins" SeDiskOperatorPrivilege -U "45LAB\bk" Enter 45LAB\bk's password: Successfully granted rights.
- You can list all users and groups who have this privilege by running:
root@ubuntu-45d:~# net rpc rights list privileges SeDiskOperatorPrivilege -U "45LAB\bk" Enter 45LAB/bk's password: SeDiskOperatorPrivilege: SeDiskOperatorPrivilege: BUILTIN\Administrators 45LAB\domain admins
Verification
- We can now communicate with our Active Directory server, and assign permissions based on the users and groups from our Active Directory.
Troubleshooting
- Ensure you have configured the server hostname and DNS address correctly.
- Ensure you have configured nsswitch.conf correctly.
Views: 2240